Difference between revisions of "CVE-2021-44228"
IVSWikiBlue (talk | contribs) |
IVSWikiBlue (talk | contribs) |
||
| Line 2: | Line 2: | ||
https://nvd.nist.gov/vuln/detail/CVE-2021-44228 | https://nvd.nist.gov/vuln/detail/CVE-2021-44228 | ||
| − | This vulnerability only | + | This vulnerability only affects VALT servers running version '''5.5''' and higher. Older VALT servers are unaffected by the vulnerability. |
=Remediation= | =Remediation= | ||
Revision as of 15:45, 13 December 2021
Vulnerability
https://nvd.nist.gov/vuln/detail/CVE-2021-44228
This vulnerability only affects VALT servers running version 5.5 and higher. Older VALT servers are unaffected by the vulnerability.
Remediation
Intelligent Video Solutions recommends that you updated your VALT server to the latest release. The latest release includes a fix to this vulnerability. You can book an update with an IVS support engineer at http://ivs.com/book.
If you are unable to update your system, you can follow the steps below to address this specific vulnerability.
WARNING: The steps below outline using an automated script to update the VALT appliance. It is designed to be used on standard Valt appliances.
WARNING: This applies to VALT 5.5 - 5.5.8. DO NOT PERFORM THESE STEPS ON ANY OTHER VERSION!!
- Log into the Valt appliance via SSH or the terminal
- Type in the following, followed by pressing Enter:
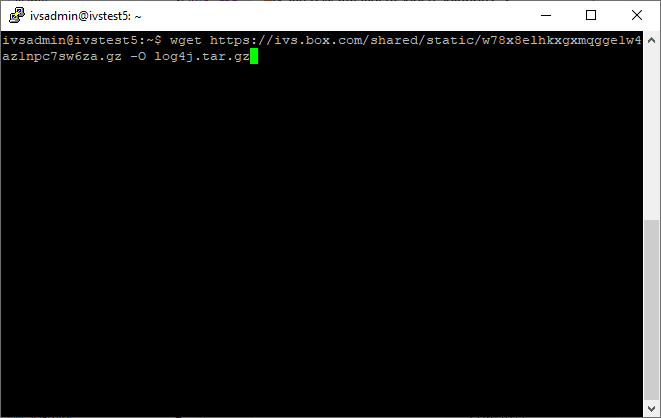
wget https://ivs.box.com/shared/static/w78x8elhkxgxmqgge1w4az1npc7sw6za.gz -O log4j.tar.gz - Type in the following, followed by pressing Enter:
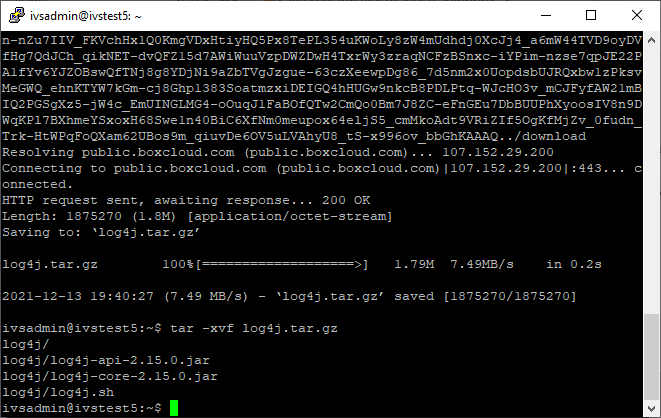
tar -xvf log4j.tar.gz - Type in the following, followed by pressing Enter:
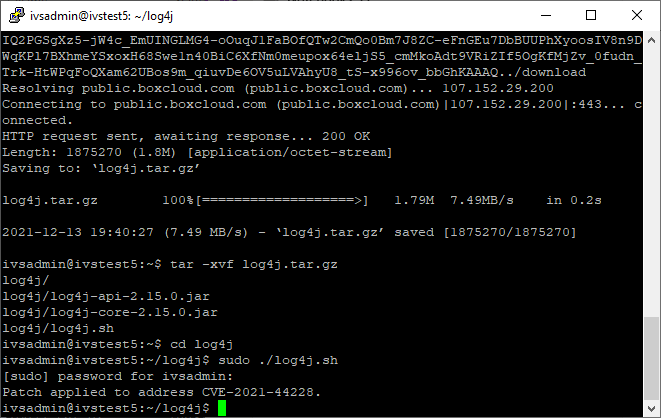
cd log4j - Type in the following, followed by pressing Enter:
sudo ./log4j.sh - Enter the password if prompted.
- The vulnerability has now been patched.