Difference between revisions of "Single Sign-On (SSO)"
IVSWikiBlue (talk | contribs) |
IVSWikiBlue (talk | contribs) |
||
| (47 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | VALT is compatible with SAML 2.0 | + | {{Article - Manual | title = SSO Configuration | content = |
| + | [[VALT SSO| ⤺ Back to VALT SSO Main Page]] | ||
| + | {{Aside - Helpful | content = VALT is compatible with <b>SAML 2.0</b>.}} | ||
| + | {{Aside | content = To access SSO on your system, you may need to reach out to our support team. [https://ivs.help IVS Support]}} | ||
| − | + | {{hr}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <h1>Scheduling a Configuration</h1> | |
| + | {{Aside - Warning | hue = 50 | content = Before configuring SSO in VALT, please make sure you've completed our [[SSO Check List]].}} | ||
| − | + | You can also schedule a <b>SSO Discovery</b> at our [https://ivs.help booking site] under <b>Schedule a Support Session</b>. During that call, we will discuss the prerequisites for configuring your VALT server to utilize SSO Authentication. | |
| − | |||
| + | {{hr}} | ||
| − | + | <h1>Authentication</h1> | |
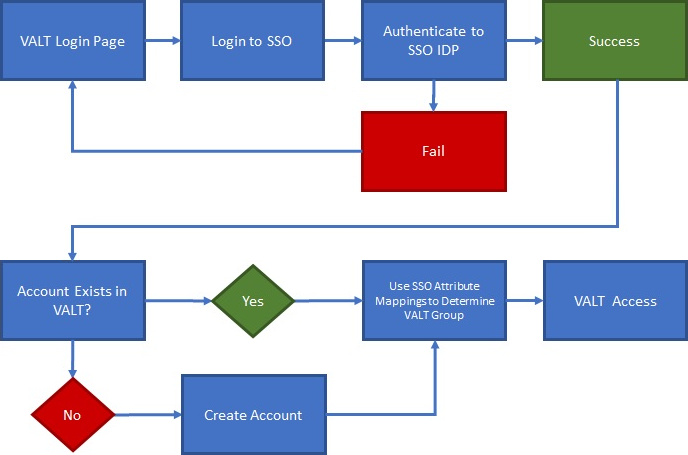
| − | + | SSO accounts are automatically created when a user logs in for the first time. The user can be placed in the proper group automatically upon login by mapping SSO attributes to a user group within VALT. | |
| − | Required: | + | *VALT's SSO uses <b>Just-In-Time (JIT) Provisioning</b>. |
| − | + | **<em>Users are reevaluated and assigned to groups each time they log in, based on a group membership attribute being passed.</em> | |
| − | + | *If a user does <u>NOT</u> have a user mapping associated with their account, the user gets moved to "<b>Users without Group</b>" and has restricted access. | |
| − | [[ | + | *If a user's user mapping changes, they will be moved to the correct group upon their next SSO sign-in. |
| + | **<em>Correct mapping is based on the SSO mapping created in VALT and the attribute/pair value being passed from the IdP.</em> | ||
| + | |||
| + | {{hr - 2}} | ||
| + | |||
| + | {{Section - Expand | title = Image Example | color = #f6c62a | content = {{img - resize | file = SSO Flow Chart.png}} }} | ||
| + | |||
| + | {{hr}} | ||
| + | |||
| + | <h1>Metadata Files</h1> | ||
| + | {{:VALT SSO - VALT's Metadata File}} | ||
| + | |||
| + | |||
| + | {{Top of Page}} | ||
| + | {{hr}} | ||
| + | |||
| + | <h1>Required Information (IdP)</h1> | ||
| + | <dl> | ||
| + | <dt>IdP Metadata File</dt> | ||
| + | <dd class="singleLineHeight">To integrate your IdP with VALT, the metadata files from both will need to be exchanged. The VALT metadata file will be generated after the IdP metadata file is uploaded to VALT.</dd> | ||
| + | {{hr - 2}} | ||
| + | <dt>User Mapping</dt> | ||
| + | <dd class="singleLineHeight">VALT's SSO uses a 1:1 mapping to add users to the correct groups. To achieve this, we require the following attributes: | ||
| + | <ul> | ||
| + | <li><strong>Unique User Identifier</strong> - This attribute will be used as the username.</li> | ||
| + | <li><strong>Groups</strong> - This attribute will be used to define which group the user is assigned to within VALT. In addition to the name of the Group attribute, VALT will need the value associated with each group that will be logging into VALT.</li> | ||
| + | <li><strong>Display Name</strong> - If the Unique User identifier does not correspond with the person's name, this attribute will set an easy-to-identify display name for the user.</li> | ||
| + | </ul></dd> | ||
| + | </dl> | ||
| + | |||
| + | |||
| + | {{Top of Page}} | ||
| + | {{hr}} | ||
| + | |||
| + | {{Manual lvl 2 | title = Optional Items | content = | ||
| + | VALT is also able to map custom attributes to some of the following fields for a user. Below are the user account fields that can be assigned through SSO. | ||
| + | |||
| + | {{hr - 2}} | ||
| + | |||
| + | <dl> | ||
| + | <dt>PIN</dt> | ||
| + | <dd class="singleLineHeight">This specifies the code used for authentication into [[BEAM Main Page|BEAM]].</dd> | ||
| + | <dd class="singleLineHeight"><em>Without one set, no pin is needed to enter BEAM</em>.</dd> | ||
| + | <dt>Card Number</dt> | ||
| + | <dd class="singleLineHeight">This specifies the card number associated with a user.</dd> | ||
| + | <dd class="singleLineHeight"><em>Only applies to customers with [[VALT Card Reader]]</em>.</dd> | ||
| + | <dt>Email</dt> | ||
| + | <dd class="singleLineHeight">The users email can also be pulled into the system.</dd> | ||
| + | <dd class="singleLineHeight"><em>If the VALT application is not connected to mail server, this field is not used for anything.</em></dd> | ||
| + | </dl> | ||
| + | }} | ||
| + | |||
| + | |||
| + | {{Top of Page}} | ||
| + | {{hr}} | ||
| + | |||
| + | <h1>Additional Settings</h1> | ||
| + | Shibboleth needs the following settings configured to function with VALT. | ||
| + | |||
| + | <table class="wikitable"> | ||
| + | <tr> | ||
| + | <th style="text-align:right;padding:0px 5px 0px 20px">signAssertions</th> | ||
| + | <td style="padding:0px 40px">true</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <th style="text-align:right;padding:0px 5px 0px 20px">signResponses</th> | ||
| + | <td style="padding:0px 40px">true</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <th style="text-align:right;padding:0px 5px 0px 20px">encryptNameIDs</th> | ||
| + | <td style="padding:0px 40px">true</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <th style="text-align:right;padding:0px 5px 0px 20px">encryptAssertions</th> | ||
| + | <td style="padding:0px 40px">false</td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | |||
| + | |||
| + | |||
| + | {{Top of Page}} | ||
| + | }} | ||
Latest revision as of 14:06, 8 April 2025
Scheduling a Configuration
You can also schedule a SSO Discovery at our booking site under Schedule a Support Session. During that call, we will discuss the prerequisites for configuring your VALT server to utilize SSO Authentication.
Authentication
SSO accounts are automatically created when a user logs in for the first time. The user can be placed in the proper group automatically upon login by mapping SSO attributes to a user group within VALT.
- VALT's SSO uses Just-In-Time (JIT) Provisioning.
- Users are reevaluated and assigned to groups each time they log in, based on a group membership attribute being passed.
- If a user does NOT have a user mapping associated with their account, the user gets moved to "Users without Group" and has restricted access.
- If a user's user mapping changes, they will be moved to the correct group upon their next SSO sign-in.
- Correct mapping is based on the SSO mapping created in VALT and the attribute/pair value being passed from the IdP.
Metadata Files
VALT's metadata.xml file is only generated after the Identity Provider (IdP) metadata file is uploaded to VALT.
To generate the IdP XML file, most providers require the Service Provider (SP) information, specifically the entityID and replyURL.
VALT's Information
- entityID
- This will be the FQDN of the server.
- Example: https://valt.ipivs.com
- replyURL
- This will be the FQDN of the server + 'saml/login_check'.
- Example: https://valt.ipivs.com/saml/login_check
Required Information (IdP)
- IdP Metadata File
- To integrate your IdP with VALT, the metadata files from both will need to be exchanged. The VALT metadata file will be generated after the IdP metadata file is uploaded to VALT.
- User Mapping
- VALT's SSO uses a 1:1 mapping to add users to the correct groups. To achieve this, we require the following attributes:
- Unique User Identifier - This attribute will be used as the username.
- Groups - This attribute will be used to define which group the user is assigned to within VALT. In addition to the name of the Group attribute, VALT will need the value associated with each group that will be logging into VALT.
- Display Name - If the Unique User identifier does not correspond with the person's name, this attribute will set an easy-to-identify display name for the user.
Optional Items
VALT is also able to map custom attributes to some of the following fields for a user. Below are the user account fields that can be assigned through SSO.
- PIN
- This specifies the code used for authentication into BEAM.
- Without one set, no pin is needed to enter BEAM.
- Card Number
- This specifies the card number associated with a user.
- Only applies to customers with VALT Card Reader.
- The users email can also be pulled into the system.
- If the VALT application is not connected to mail server, this field is not used for anything.
Additional Settings
Shibboleth needs the following settings configured to function with VALT.
| signAssertions | true |
|---|---|
| signResponses | true |
| encryptNameIDs | true |
| encryptAssertions | false |