Difference between revisions of "Single Sign-On (SSO)"
IVSWikiBlue (talk | contribs) (→To configure SSO VALT needs the following information:) |
IVSWikiBlue (talk | contribs) |
||
| Line 1: | Line 1: | ||
<div class="floating_card">VALT is compatible with SAML 2.0</div> | <div class="floating_card">VALT is compatible with SAML 2.0</div> | ||
| − | + | {{Section | content = | |
| − | + | *Browse to the the Fully qualified domain name and sign in with a local account | |
| + | *Click on admin | ||
| + | *Click on Users & Groups | ||
| + | *Along the top click on SSO and add SAML config | ||
| − | + | <hr> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | < | ||
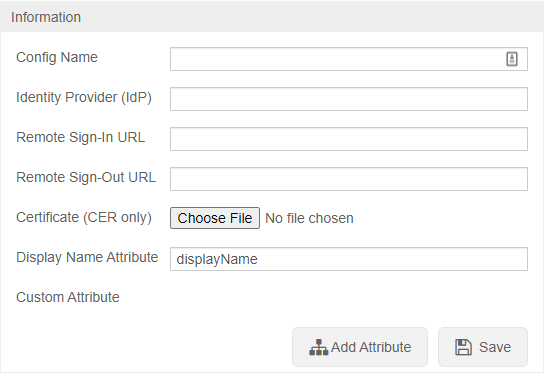
==To configure SSO VALT needs the following information:== | ==To configure SSO VALT needs the following information:== | ||
| − | |||
*Certificate in .cer format | *Certificate in .cer format | ||
*Identity Provider (IDP) | *Identity Provider (IDP) | ||
| Line 32: | Line 29: | ||
signResponses: true | signResponses: true | ||
encryptNameIDs: true | encryptNameIDs: true | ||
| − | < | + | |
| + | <hr> | ||
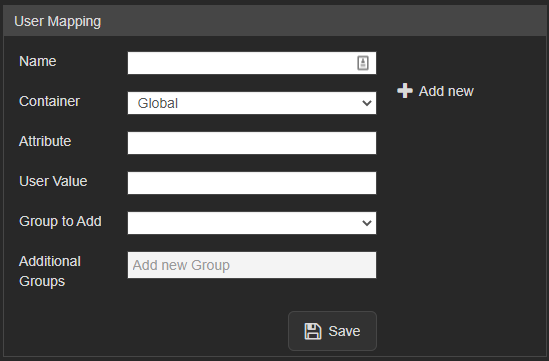
==User Mapping== | ==User Mapping== | ||
<div class="floating_card">User mapping is used to map groups in the customer's system to groups within VALT</div> | <div class="floating_card">User mapping is used to map groups in the customer's system to groups within VALT</div> | ||
| − | |||
Required: | Required: | ||
*Attribute (The item that gets passed back to VALT) | *Attribute (The item that gets passed back to VALT) | ||
| Line 45: | Line 42: | ||
Items to Note: | Items to Note: | ||
*SSO in VALT is a one to one mapping for groups | *SSO in VALT is a one to one mapping for groups | ||
| − | + | }} | |
Revision as of 14:59, 22 August 2023
VALT is compatible with SAML 2.0