Difference between revisions of "Template:Network Architecture"
IVSWikiBlue (talk | contribs) |
IVSWikiBlue (talk | contribs) |
||
| Line 1: | Line 1: | ||
{{Section | title = <h1>Network Architecture</h1> | content = | {{Section | title = <h1>Network Architecture</h1> | content = | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
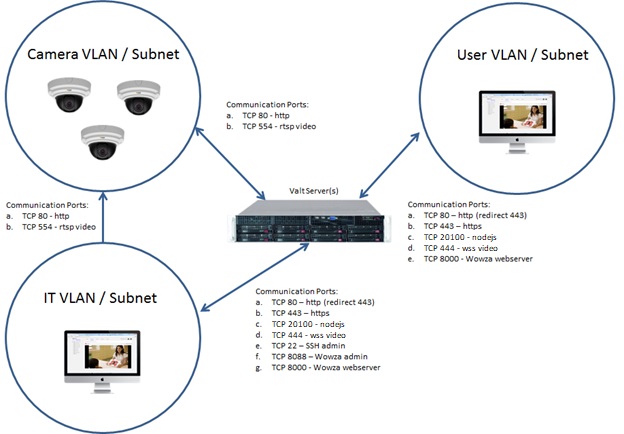
Below is a diagram of a sensitive network environment, where in-transit encryption is a requirement. This type of network architecture is typical of environments that are using the system to capture / observe actual patient interactions within clinical training environments. | Below is a diagram of a sensitive network environment, where in-transit encryption is a requirement. This type of network architecture is typical of environments that are using the system to capture / observe actual patient interactions within clinical training environments. | ||
| − | |||
{{img - no_click | file = specific-8.jpg}} | {{img - no_click | file = specific-8.jpg}} | ||
| − | |||
| − | |||
| − | |||
| − | {{ | + | {{Aside | content = For SSL, we will need the customer to set up a DNS name for the server <em>(example ivs-valt.mysite.edu)</em>. We will also need a wildcard or generated signed certificate that is compatible with nginx and can be applied by an IVS engineer. LetsEncrypt may also be utilized.}} |
}} | }} | ||