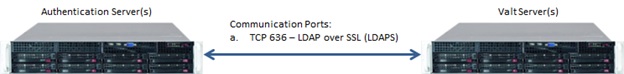
The network architecture for a VALT solution can look different for many of our customers.
Below is a typical standard suggested network architecture diagram. We see this architecture often used in Law Enforcement & Simulation, as well as other environments, where security is important and segmenting access to only the necessary ports / devices is desired but in transit encryption is not a requirement.
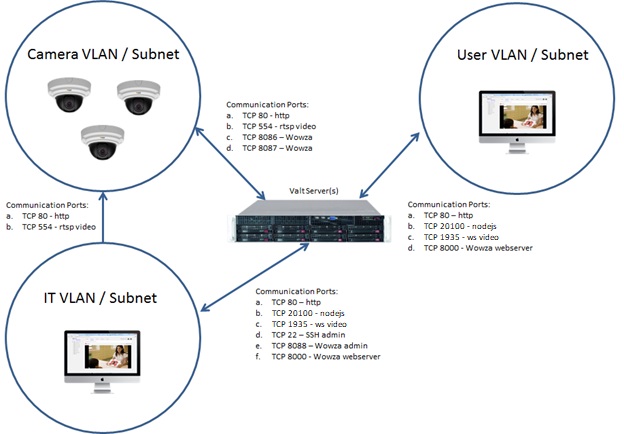
If LDAP is being used, the server will also need access to the authentication server(s) as shown below. For LDAP integration using our software, we will also need a bind account and password with read-only access to LDAP.
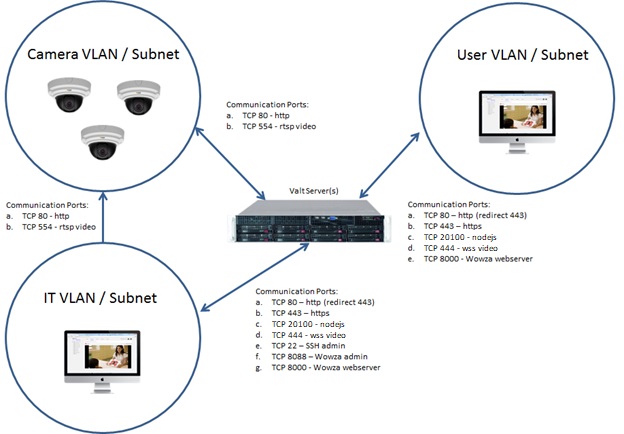
Below is a diagram of a sensitive network environment, where in-transit encryption is a requirement. This type of network architecture is typical of environments that are using the system to capture / observe actual patient interactions within clinical training environments.
For SSL, we will need the customer to set up a DNS name for the server (example ivs-valt.mysite.edu). We will also need a wildcard or generated signed certificate that is compatible with apache and can be applied by an IVS engineer.
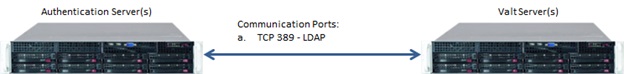
If LDAP is being used, the server will also need access to the authentication server(s) as shown below. For LDAP integration within our software, we will also need a bind account and password with read-only access to LDAP.