Difference between revisions of "Single Sign-On (SSO)"
IVSWikiBlue (talk | contribs) |
IVSWikiBlue (talk | contribs) |
||
| Line 24: | Line 24: | ||
*To migrate current users to SSO the SQL command needs to be run on the database with the correct group ID<pre>UPDATE users set ldap_sync_id = NULL, saml_config_id = 1, userType = 'local' where deleted_at is null and group_id =</pre> | *To migrate current users to SSO the SQL command needs to be run on the database with the correct group ID<pre>UPDATE users set ldap_sync_id = NULL, saml_config_id = 1, userType = 'local' where deleted_at is null and group_id =</pre> | ||
*Custom Attributes can be usernames if you want to map to something specific or other information that you want to pull into VALT | *Custom Attributes can be usernames if you want to map to something specific or other information that you want to pull into VALT | ||
| − | + | *Shibboleth IDP's need the following settings specified: | |
| + | signAssertions: true | ||
| + | signResponses: true | ||
| + | encryptAssertions: false | ||
| + | encryptNameIDs: true | ||
==User Mapping== | ==User Mapping== | ||
Revision as of 10:13, 5 August 2020
VALT is compatible with SAML 2.0
- Browse to the the Fully qualified domain name and sign in with a local account
- Click on admin
- Click on Users & Groups
- Along the top click on SSO and add SAML config
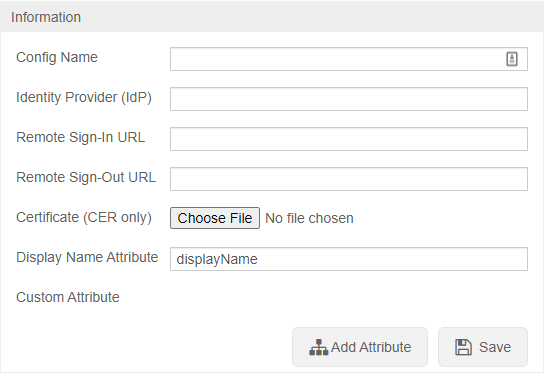
To configure SSO VALT needs the following information:
- Certificate in .cer format
- Identity Provider (IDP)
- Remote Sign-In URL
- Remote Sign-Out URL
- Display Name Attribute
- Any other custom attributes needed
After SSO is configured browse to Replace with VALT Server Address/saml/metadata.xml to grab the VALT metadata to add to your system
Items to Note:
- If moving from LDAP to SSO you have to add a custom attribute to map to the username so the usernames will match correctly
- To migrate current users to SSO the SQL command needs to be run on the database with the correct group ID
UPDATE users set ldap_sync_id = NULL, saml_config_id = 1, userType = 'local' where deleted_at is null and group_id =
- Custom Attributes can be usernames if you want to map to something specific or other information that you want to pull into VALT
- Shibboleth IDP's need the following settings specified:
signAssertions: true signResponses: true encryptAssertions: false encryptNameIDs: true
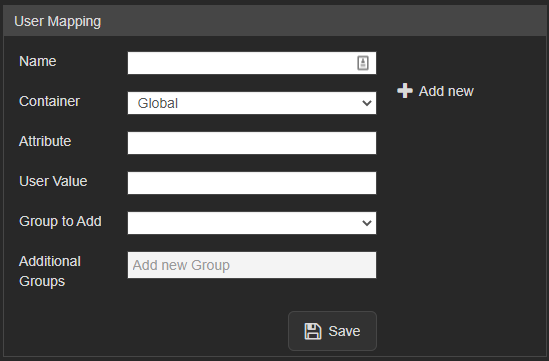
User Mapping
User mapping is used to map groups in the customer's system to groups within VALT
Required:
- Attribute (The item that gets passed back to VALT)
- User Value (The value of the item that gets passed back to VALT)
Items to Note:
- SSO in VALT is a one to one mapping for groups