Difference between revisions of "Strict Transport Security"
IVSWikiBlue (talk | contribs) (Created page with "=Symptoms= On a VALT server with HTTPS enabled, when you attempt to download, the page spins for a few seconds and then goes to a "This site cannot be reached" message. Fi...") |
(No difference)
|
Revision as of 09:48, 22 March 2021
Symptoms
On a VALT server with HTTPS enabled, when you attempt to download, the page spins for a few seconds and then goes to a "This site cannot be reached" message.
When examing the address bar you will note that the address is similar to:
Cause
This issue is caused by the Strict-Transport-Security header being set.
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains
This header might be set in the /etc/apache2/sites-enabled/default-ssl.conf or /etc/apache2/sites-enabled/v3.conf config files. It could also be set on another website with the same domain as the VALT server. If the includeSubDomains flag is set on the header, it will affect all sites that share the root domain.
In previous versions of chromium (which most browsers are based on) the Strict-Transport-Security header only affected traffic on standard ports. The download for VALT uses port 8000 and was previously excluded from this setting.
Verification
Google Chrome
- Enter the following in the address bar:
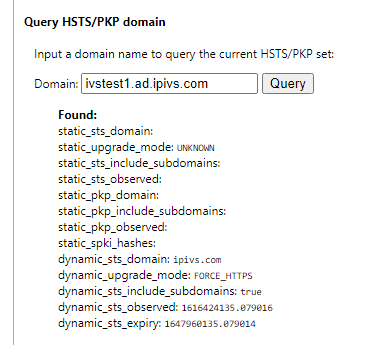
- In the Query HSTS/PKP domain section, enter the fqdn of the VALT server and click query.
- If something similar to what is shown in the picture above is displayed then hsts is enabled.
- Note: If the header was sent on another website in the same domain, it may not show just by querying the address of the valt server. You may need to try other queries, such as just the root domain
Resolution
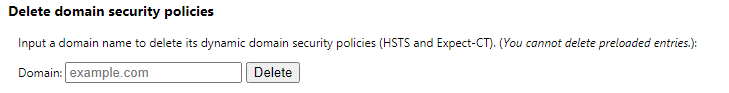
The issue can be temporarily resolved by entering the site into the Delete domain security policies and clicking delete.
The site entered should be the sts_domain shown when querying during verification. In the example above it is ipivs.com
This will only work until the next time the header is recieved. If this header is set in the apache config files it MUST be removed and apache must be restarted. If this header is being sent from another website in the same domain, the header must be removed from that site or care must be taken not to visit that site. There does not appear to be any work around to this issue at this time.