Difference between revisions of "CVE-2021-44228"
IVSWikiBlue (talk | contribs) (Created page with " '''WARNING: The steps below outline using an automated script to update the VALT appliance. It is designed to be used on standard Valt appliances. # Log into the Valt appli...") |
IVSWikiBlue (talk | contribs) |
||
| Line 1: | Line 1: | ||
| − | '''WARNING: The steps below outline using an automated script to update the VALT appliance. It is designed to be used on standard Valt appliances. | + | |
| + | '''WARNING: The steps below outline using an automated script to update the VALT appliance. It is designed to be used on standard Valt appliances.''' | ||
| + | |||
| + | '''WARNING: This applies to VALT 5.5 - 5.5.8. DO NOT PERFORM THESE STEPS ON ANY OTHER VERSION!! | ||
# Log into the Valt appliance via SSH or the terminal | # Log into the Valt appliance via SSH or the terminal | ||
Revision as of 13:54, 13 December 2021
WARNING: The steps below outline using an automated script to update the VALT appliance. It is designed to be used on standard Valt appliances.
WARNING: This applies to VALT 5.5 - 5.5.8. DO NOT PERFORM THESE STEPS ON ANY OTHER VERSION!!
- Log into the Valt appliance via SSH or the terminal
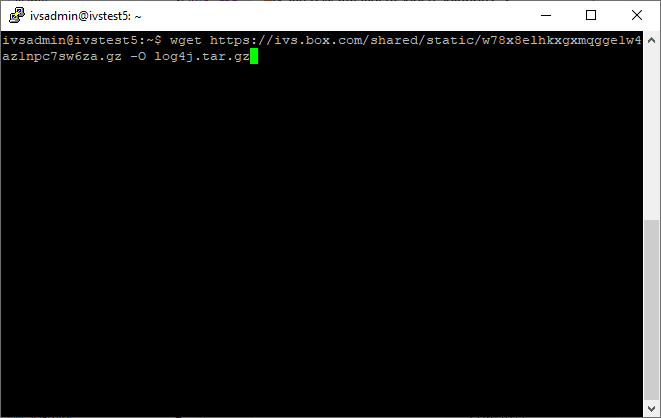
- Type in the following, followed by pressing Enter:
wget https://ivs.box.com/shared/static/w78x8elhkxgxmqgge1w4az1npc7sw6za.gz -O log4j.tar.gz - Type in the following, followed by pressing Enter:
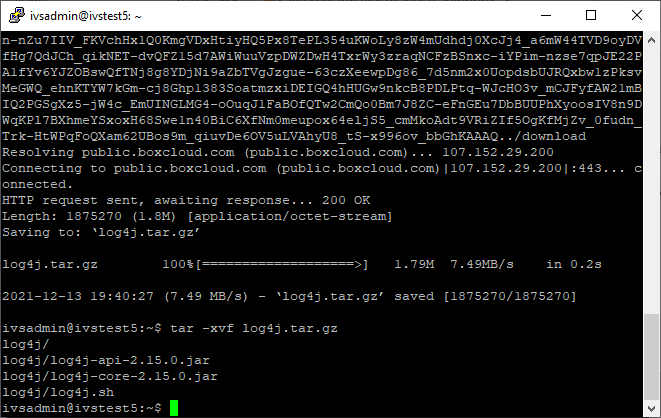
tar -xvf log4j.tar.gz - Type in the following, followed by pressing Enter:
cd log4j - Type in the following, followed by pressing Enter:
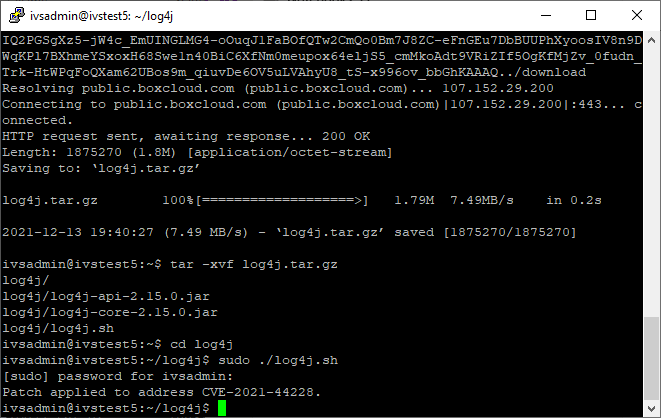
sudo ./log4j.sh - Enter the password if prompted.
- The vulnerability has now been patched.