Set up an Encrypted Volume for Video Storage
WARNING: The following procedure will delete all video files on your Valt appliance. Make sure to copy all video files off the VALT server prior to following the steps below. Video files can be copied back after completing the procedure below. Additionally if the key/passphrase is lost you will not be able to access the video files. IVS is not responsible for maintaining keys or passphrases.
Identify/Create a Partition
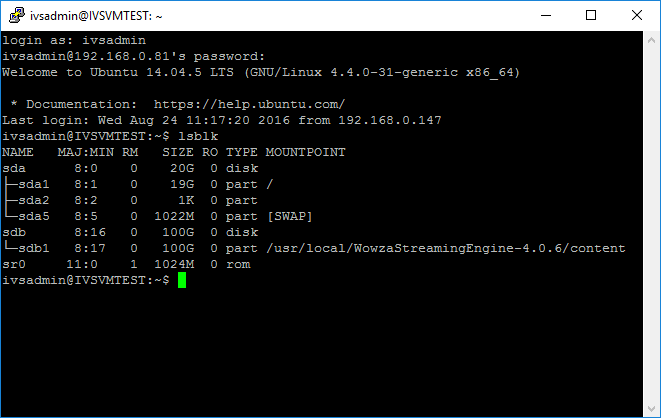
In order to encrypt the video storage, you will need a separate partition for storing the video files. If you have not done so already, create a partition to be encrypted. By default most Valt appliances have a single partition that spans the entire RAID array for video storage. You can see the partitions currently on your VALT server by issuing the following command from a terminal session.sudo lsblk
- In the picture above sdb1 is currently being used for video storage as it is currently mounted in /usr/local/WowzaStreamingEngine-4.0.6/content.
Encrypt the Partition
- Connect to the server via SSH, or log in to the terminal
- It is highly recommended that you connect via ssh so you can copy and paste the commands below
- Type in the following, and press Enter:
sudo apt-get install cryptsetup -y
- Type in the following, and press Enter:
sudo cryptsetup luksFormat /dev/sdb1
- Be sure to replace /dev/sdb1 with the correct partition name
- You will be prompted to enter a passphrase to encrypt the drive.
- Type in the following, and press Enter:
sudo cryptsetup open /dev/sdb1 videostorage
- Type in the following, and press Enter:
sudo mkfs -t ext4 /dev/mapper/videostorage
- Type in the following, and press Enter:
sudo blkid
- This will display the UUIDs for each partition. Note the UUID for the partition you encrypted (ex: /dev/sdb1).
- Type in the following, and press Enter:
sudo nano /etc/crypttab
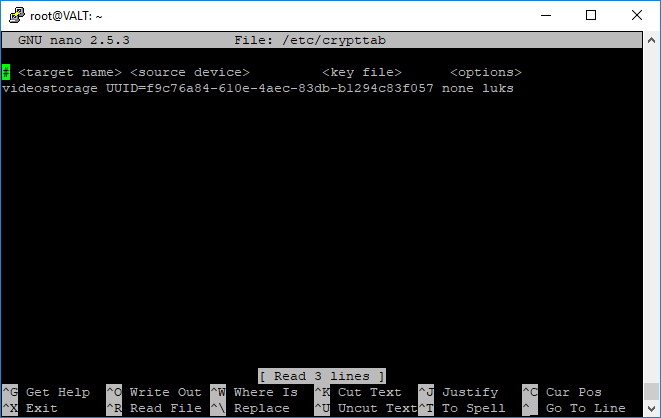
- Add a line for the encrypted video partition. It should read similar to the following:
videostorage UUID=f9c76a84-610e-4aec-83db-b1294c83f057 none luks
- Press CTRL-X.
- Enter Y to save.
- Do not change the file name and press Enter.
- Type in the following, and press Enter:
sudo nano /etc/fstab
- Press CTRL-X.
- Enter Y to save.
- Do not change the file name and press Enter.
- Type in the following, and press Enter:
sudo mount -a
- Type in the following, and press Enter:
sudo lsblk
- The results should be similar to the above picture, where sdb1 is mounted under /usr/local/WowzaStreamingEngine-4.0.6/content
- Type in the following, and press Enter:
cd /home/ivsadmin/ValtInstall
- Type in the following, and press Enter:
sudo ./Storage
- Type in the following, and press Enter:
sudo reboot
Use a Key to Decrypt the Drive
WARNING: The following directions will allow you to decrypt the drive automatically on boot without needing a password entered at the console. The key will be stored on the OS drive. If this key is compromised the videos can be decrypted without need to enter a passphrase.
- Type in the following, and press Enter:
sudo mkdir /etc/luks-keys
- Type in the following, and press Enter:
sudo dd if=/dev/urandom of=/etc/luks-keys/videostorage_key bs=512 count=8
- Type in the following, and press Enter:
sudo cryptsetup -v luksAddKey /dev/sdb1 /etc/luks-keys/videostorage_key
- You will be prompted to enter the passphrase for the disk.
- Type in the following, and press Enter:
sudo nano /etc/crypttab
- Modify the line for the encrypted video partition. It should read similar to the following when you have changed it:
videostorage UUID=f9c76a84-610e-4aec-83db-b1294c83f057 /etc/luks-keys/videostorage_key luks