Difference between revisions of "Troubleshoooting LDAP"
IVSWikiBlue (talk | contribs) (→Validate LDAP Query/Credentials) |
IVSWikiBlue (talk | contribs) (→Verify Distinguished Name of Groups) |
||
| Line 38: | Line 38: | ||
If you believe the distinguished name of the group is incorrect you can verify it by accessing the customer's directory using [http://www.ldapadmin.org/ LDAP Admin] and the credentials they have provided you. | If you believe the distinguished name of the group is incorrect you can verify it by accessing the customer's directory using [http://www.ldapadmin.org/ LDAP Admin] and the credentials they have provided you. | ||
# Download and run LDAP Admin | # Download and run LDAP Admin | ||
| + | #: [[File:LDAPT6.png]] | ||
# Click '''Connect''' | # Click '''Connect''' | ||
| + | #: [[File:LDAPT7.png]] | ||
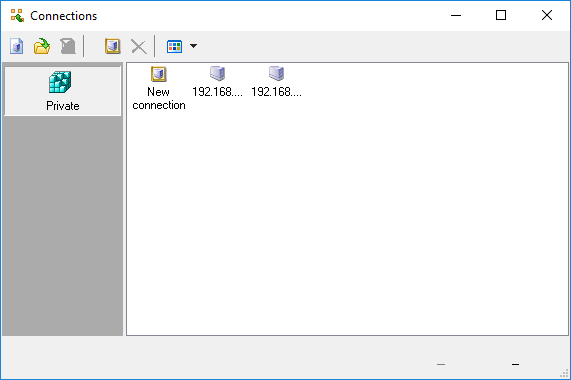
# Double click on '''New Connection''' | # Double click on '''New Connection''' | ||
| + | #: [[File:LDAPT5.png]] | ||
# Enter the host | # Enter the host | ||
# Uncheck Anonymous Connection | # Uncheck Anonymous Connection | ||
| Line 46: | Line 49: | ||
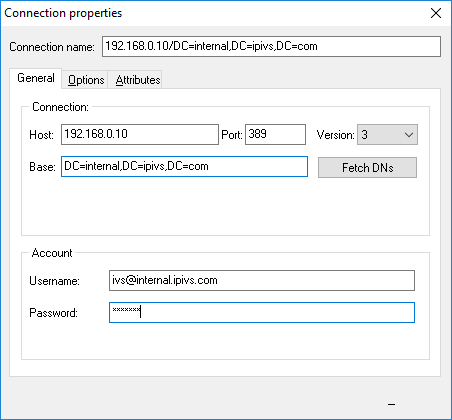
# Select the Base DN for the domain | # Select the Base DN for the domain | ||
#: EX: DC=internal,DC=ipivs,DC=com | #: EX: DC=internal,DC=ipivs,DC=com | ||
| + | #: [[File:LDAPT8.png]] | ||
# Click OK | # Click OK | ||
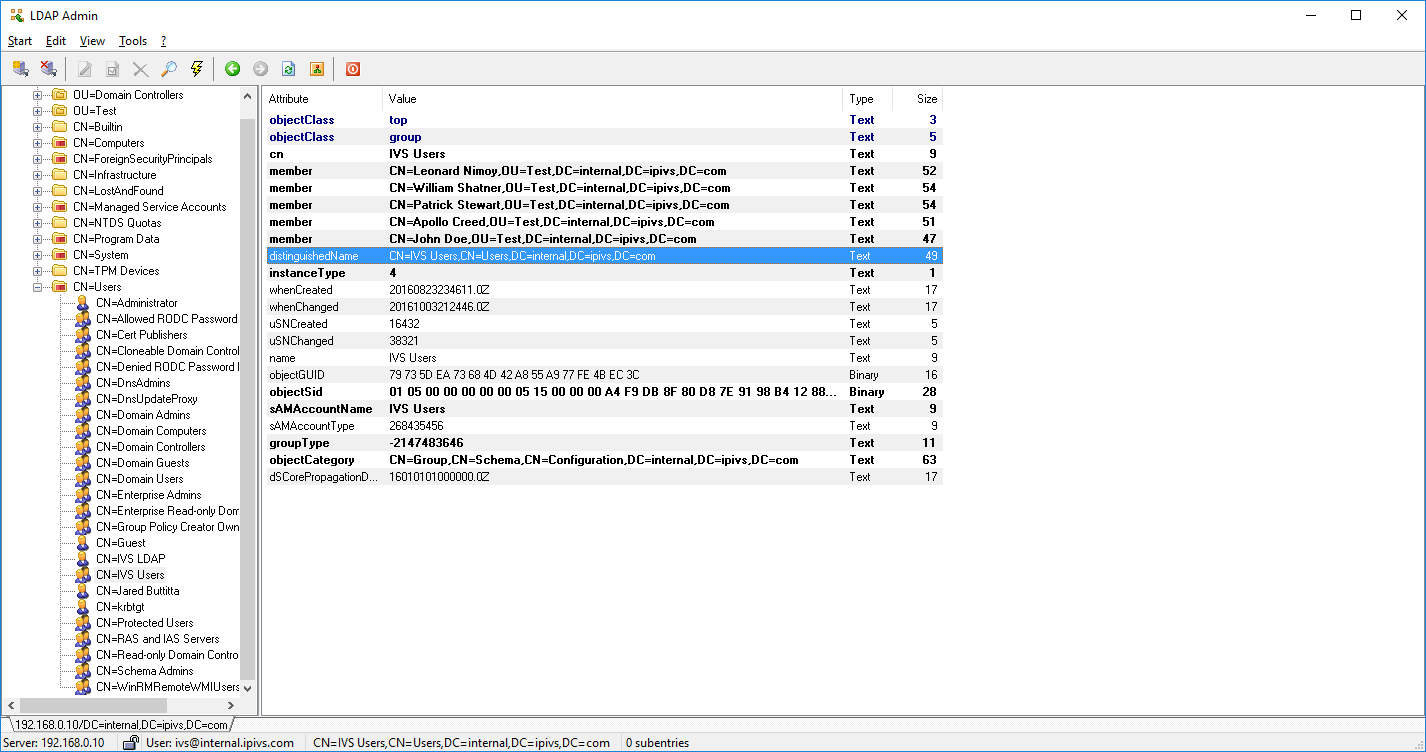
# You can now browse the customer's directory. Using the distinguished name you were provided, try to locate the group. | # You can now browse the customer's directory. Using the distinguished name you were provided, try to locate the group. | ||
| + | #: [[File:LDAPT10.png]] | ||
#* If you are able to locate the group, click on it and the DN will be displayed on the right hand side of the window. | #* If you are able to locate the group, click on it and the DN will be displayed on the right hand side of the window. | ||
#* If you are unable to locate the group, contact the customer's IT department. | #* If you are unable to locate the group, contact the customer's IT department. | ||
| + | |||
=TLS 1.2 Issues= | =TLS 1.2 Issues= | ||
There is a known compatibility issue between OpenLDAP and certain versions of Windows Server. This issue was resolved in hotfixes, however you if you are able to verify all the information is correct and you are still unable to submit an LDAP query via LDAPS, this may be the cause. The issue stems from a compatibility problem related to TLS 1.2. By disabling TLS version 1.2 you can force LDAPS to use TLS version 1.1. | There is a known compatibility issue between OpenLDAP and certain versions of Windows Server. This issue was resolved in hotfixes, however you if you are able to verify all the information is correct and you are still unable to submit an LDAP query via LDAPS, this may be the cause. The issue stems from a compatibility problem related to TLS 1.2. By disabling TLS version 1.2 you can force LDAPS to use TLS version 1.1. | ||
Revision as of 13:50, 9 February 2017
Often times configuring the Valt appliance for LDAP authentication can prove challenging. Most often these issues are caused by communications problems, incorrect credentials or using the wrong distinguished name. In order to troubleshoot the issue, it's recommended you take the Valt application out of the equation.
Contents
Validate Connection
- Connect to the Valt server via SSH or access the terminal.
- If accessing via the terminal, you will need to exit to shell
- Ping the LDAP server
- EX: Ping ldap.ipivs.com
- If the server responds you are able communicate with that server.
- If the server does not respond, you may have a networking issue, or ICMP may be blocked. You may need to contact the customer's IT department to investigate. If ICMP is just blocked, you do not need ICMP in order to perform LDAP queries.
- Verify you have the correct server address and check if the server is set to accept queries via LDAP or LDAPS
- Check to see if the VALT server can communicate with the LDAP server on the appropriate port.
- For LDAP: nc -zv ldapserver 389
- This command should return "Connection to ldapserver 389 port [tcp/ldap] succeeded!"
- For LDAPS: nc -zv ldapserver 636
- This command should return "Connection to ldapserver 636 port [tcp/ldaps] succeeded!"
- If the appropriate command returns a failure message, the VALT server is unable to communicate with the ldap server on the appropriate port. This could be caused by a firewall or other security appliance between the two servers or you may have the incorrect LDAP server. You should contact the customer's IT department and notify them that the Valt server is unable to connect to the provided LDAP server on the appropriate port.
- For LDAP: nc -zv ldapserver 389
Validate LDAP Query/Credentials
After verifying communication between the VALT server and the LDAP server, you can validate the credentials you were provided by attempting to connect to the LDAP server from the command line.
- Connect to the Valt server via SSH or access the terminal.
- If accessing via the terminal, you will need to exit to shell
- ldapsearch -H ldap://ldapserver -x -b "distinguishedname" -D username -W
- Be sure to replace the italicized text with the appropriate information.
- Example:
- LDAP Server: ivs2012r2dc.internal.ipivs.com
- Protocol: LDAPS
- Distinguished Name of Group: CN=IVS Users,CN=Users,DC=internal,DC=ipivs,DC=com
- Username: ivs@internal.ipivs.com
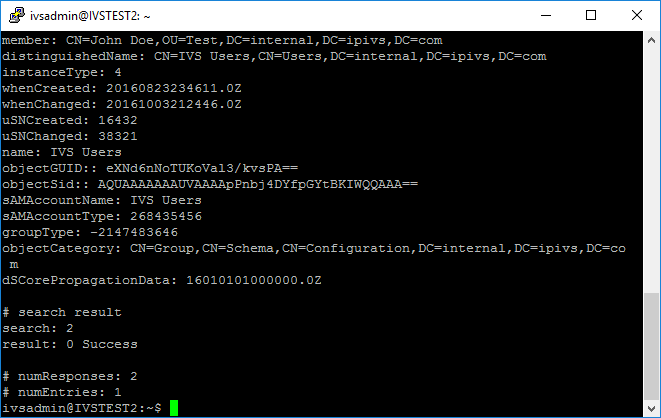
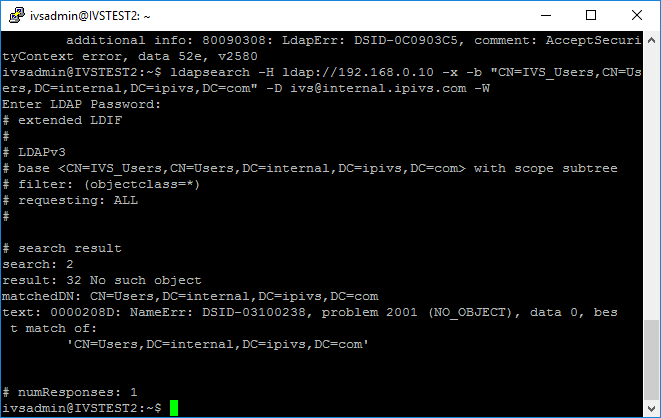
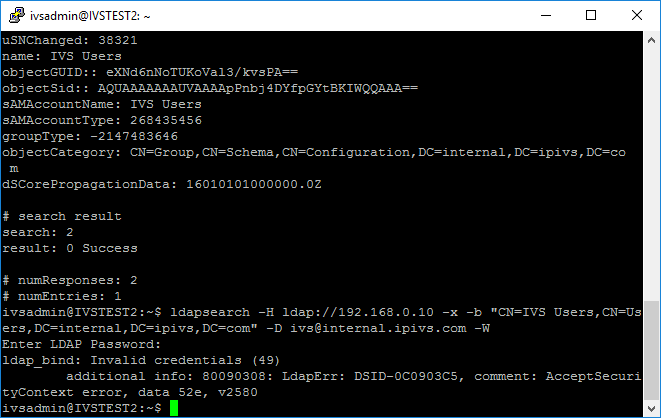
- ldapsearch -H ldaps://ivs2012r2dc.internal.ipivs.com -x -b "CN=IVS Users,CN=Users,DC=internal,DC=ipivs,DC=com" -D ivs@internal.ipivs.com -W
- Enter the password when prompted.
- The query should return a list of group members.
- If a list of group members was returned successfully, then LDAP authentication should be working. If you are still experiencing issues it is most likely a configuration problem with the application.
- If you received a message stating "No Such Object," the distinguished name of the group you entered is incorrect. The next section contains information on verifying the distinguished name or the group, or you can contact the customer's IT department.
- If you received a message stating "Invalid credentials," the username or password you entered is incorrect. You will need to contact the customer's IT department.
Verify Distinguished Name of Groups
If you believe the distinguished name of the group is incorrect you can verify it by accessing the customer's directory using LDAP Admin and the credentials they have provided you.
- Download and run LDAP Admin
- Click Connect
- Double click on New Connection
- Enter the host
- Uncheck Anonymous Connection
- Enter the username and password
- Click Fetch DNs
- Select the Base DN for the domain
- Click OK
- You can now browse the customer's directory. Using the distinguished name you were provided, try to locate the group.
- If you are able to locate the group, click on it and the DN will be displayed on the right hand side of the window.
- If you are unable to locate the group, contact the customer's IT department.
TLS 1.2 Issues
There is a known compatibility issue between OpenLDAP and certain versions of Windows Server. This issue was resolved in hotfixes, however you if you are able to verify all the information is correct and you are still unable to submit an LDAP query via LDAPS, this may be the cause. The issue stems from a compatibility problem related to TLS 1.2. By disabling TLS version 1.2 you can force LDAPS to use TLS version 1.1.
To test if this is the case, run the following:
- export LDAPTLS_CIPHER_SUITE=NORMAL:!VERS-TLS1.2
- Run another LDAPSearch
- If the search is successful, the compatibility issue is causing your problem.
You will need to modify the LDAP PHP files to include the line putenv(‘LDAPTLS_CIPHER_SUITE=NORMAL:!VERS-TLS1.2’);
The following files will need to be modified:
- /var/www/v3/src/FS/UserBundle/Util/LdapSynchronizer.php
- /var/www/v3/src/FS/UserBundle/Controller/LDAPController.php
- /var/www/v3/src/FS/CamBundle/Command/LdapSyncCommand.php
- /var/www/v3/src/FS/UserBundle/Entity/LdapServer.php
- /var/www/v3/src/FS/UserBundle/Entity/LdapSynchronize.php
- /var/www/v3/src/FS/UserBundle/Entity/User.php
- /var/www/v3/app/console
This list of files was from old notes and may not be 100% accurate